转载请注明出处,本文仅用于学习交流,不对之处,恳请指正 ,部分图片摘取网络,如有侵权请联系
!!!注意!!! 本文介绍的方式是在服务端中安装使用
安装FRP或Fail2ban
-
使用FRP的方式请参考我以往这篇文章Frp(高性能反向代理应用)
-
安装Fail2ban的方式以及常规的SSH防爆破可以参考我以往的这篇文章使用Fail2ban自动拉黑暴力破解SSH的IP
FRP防爆规则配置文件
需要注意的是,以下的规则是使用正则匹配对应的服务名称,所以FRPC启用的名称需要相应匹配,比如SSH服务的FRPC启动服务名为HOME_SSH,则正则为
failregex = ^.*\[.*HOME_SSH.*\] get a user connection \[<HOST>:[0-9]*\]为了通用性更高,我直接使用的为SSH,FTP,RDP等通用名称,但可能存在误伤,请酌情调整你的正则代码
Frp的日志时间刚好是Fail2ban能够识别的格式,所以我们并不需要特意定制时间格式如果你要定制日志时间格式可以使用如下代码,注意%需要使用%%代替
[Init] datepattern = %%Y/%%m/%%d %%H:%%M:%%S
防SSH爆破规则文件
-
编写规则配置文件
注意规则文件名称,下面定义配置文件时需要使用
nano /etc/fail2ban/filter.d/frps-ssh-ban.conf -
写入以下代码
[Definition] failregex = ^.*\[.*SSH.*\] get a user connection \[<HOST>:[0-9]*\] ignoreregex =
防FTP爆破规则配置文件
-
编写规则文件
注意规则文件名称,下面定义配置文件时需要使用
nano /etc/fail2ban/filter.d/frps-ftp-ban.conf -
写入以下代码
[Definition] failregex = ^.*\[.*FTP_21.*\] get a user connection \[<HOST>:[0-9]*\] ignoreregex =
防RDP爆破规则配置文件
-
编写规则文件
注意规则文件名称,下面定义配置文件时需要使用
nano /etc/fail2ban/filter.d/frps-rdp-ban.conf -
写入以下代码
[Definition] failregex = ^.*\[.*RDP.*\] get a user connection \[<HOST>:[0-9]*\] ignoreregex =
FRP防爆破配置文件
-
编辑配置文件
nano /etc/fail2ban/jail.local -
写入以下代码
请酌情调整你的配置文件代码
# FRP SSH防爆破 [frps-ssh-ban] # 是否启用 enabled = true # 检测时长 findtime = 3m # 允许的最大重试次数,超过则封锁 maxretry = 3 # 封锁时长 bantime = 120m # 过滤规则文件,即上面定义的规则文件 filter = frps-ssh-ban # 存放日志的路径 logpath = /var/log/frps.log # 匹配协议 protocol = all # 端口号 port = all # 拦截动作(基于iptables) chain = all action = iptables-allports[name=frps,protocol=tcp] # FRP RDP防爆破 [frps-rdp-ban] # 是否启用 enabled = true # 检测时长 findtime = 3m # 允许的最大重试次数,超过则封锁 maxretry = 6 # 封锁时长 bantime = 30m # 过滤规则文件,即上面定义的规则文件 filter = frps-rdp-ban # 存放日志的路径 logpath = /var/log/frps.log # 匹配协议 protocol = all # 端口号 port = all # 拦截动作(基于iptables) chain = all action = iptables-allports[name=frps,protocol=tcp] # FRP FTP防爆破 [frps-ftp-ban] # 是否启用 enabled = true # 检测时长 findtime = 5m # 允许的最大重试次数,超过则封锁 maxretry = 30 # 封锁时长 bantime = 60m # 过滤规则文件,即上面定义的规则文件 filter = frps-ftp-ban # 存放日志的路径 logpath = /var/log/frps.log # 匹配协议 protocol = all # 端口号 port = all # 拦截动作(基于iptables) chain = all action = iptables-allports[name=frps,protocol=tcp] -
重启服务
fail2ban-client reload # 或者直接 # systemctl restart fail2ban.service
测试
-
验证fail2ban是否成功运行
sudo fail2ban-client ping返回
Server replied: pong -
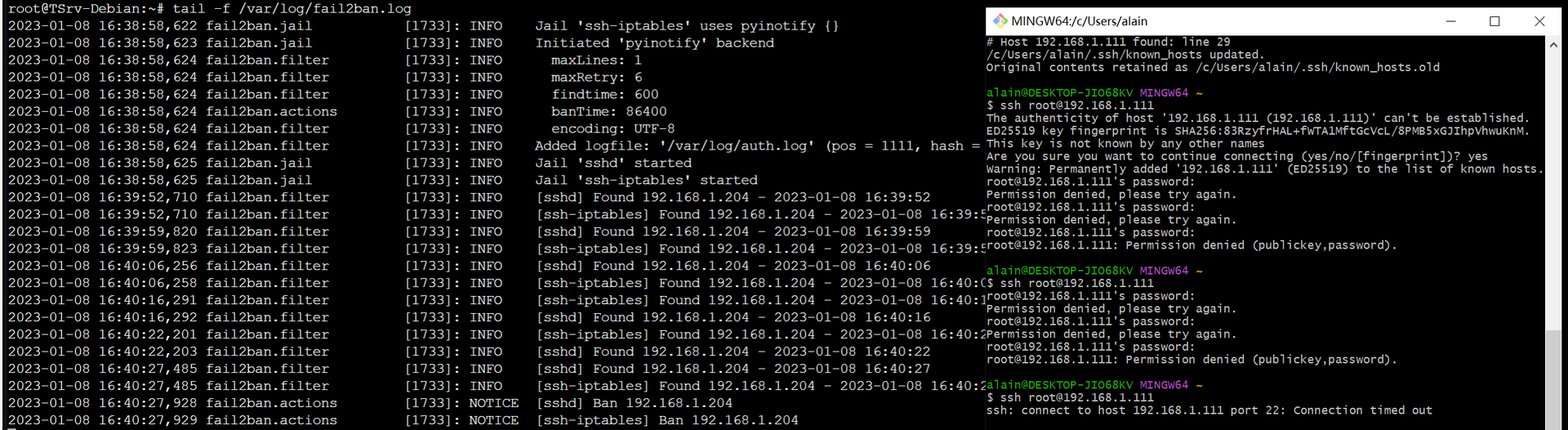
测试并查看日志文件
多次输入错误密码并重连
图片我直接用了原来的查看日志
sudo tail -f /var/log/fail2ban.log
查看被Fail2ban封锁的IP
-
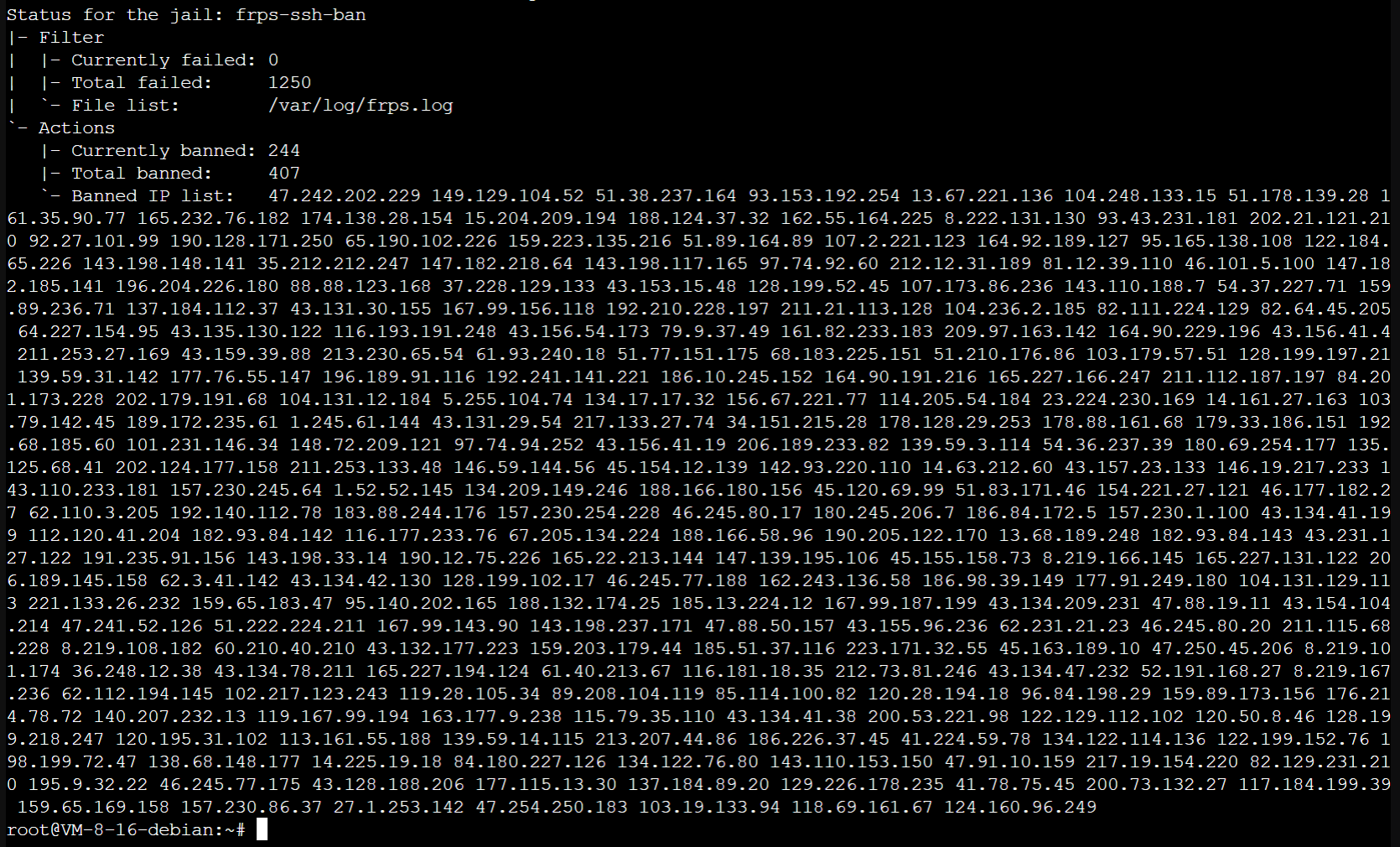
查看SSH被Fail2ban封锁的IP
被拉黑的数量是真的不少
sudo fail2ban-client status frps-ssh-ban -
查看RDP被Fail2ban封锁的IP
sudo fail2ban-client status frps-rdp-ban -
查看FTP被Fail2ban封锁的IP
sudo fail2ban-client status frps-ftp-ban
解封IP
sudo fail2ban-client set sshd unbanip 192.168.1.110
文章评论
老哥,我照你的教程配置启动后,f2b的日志总有这个报错,感觉这个配置好像执行不了,我用的是centos 7.9,firewalld+fail2ban,fail2ban的jail.local部分模块如下:
[DEFAULT]
ignoreip = 127.0.0.1/8
bantime = 86400
findtime = 300
maxretry = 5
backend = auto
banaction = firewallcmd-ipset
action = %(action_mwl)s
# FRP SSH防爆破
[frps-ssh-ban]
enabled = true
findtime = 3m
maxretry = 3
filter = frps-ssh-ban
logpath = /root/frp_0.48.0/frps.log
port = http,https
action = %(action_mwl)s
报错信息fail2ban.log:
2023-07-22 15:15:50,489 fail2ban.actions [16741]: NOTICE [frps-ssh-ban] Restore Ban 117.141.150.30
2023-07-22 15:15:51,236 fail2ban.utils [16741]: ERROR 7ff463a21ed0 -- exec: ipset create f2b-frps-ssh-ban hash:ip timeout 0
firewall-cmd --direct --add-rule ipv4 filter all 0 -p tcp -m multiport --dports "$(echo 'http,https' | sed s/:/-/g)" -m set --match-set f2b-frps-ssh-ban src -j REJECT --reject-with icmp-port-unreachable
2023-07-22 15:15:51,236 fail2ban.utils [16741]: ERROR 7ff463a21ed0 -- stderr: 'ipset v7.1: Set cannot be created: set with the same name already exists'
2023-07-22 15:15:51,236 fail2ban.utils [16741]: ERROR 7ff463a21ed0 -- stderr: "Error: COMMAND_FAILED: '/usr/sbin/iptables-restore -w -n' failed: iptables-restore: line 2 failed"
2023-07-22 15:15:51,236 fail2ban.utils [16741]: ERROR 7ff463a21ed0 -- stderr: ''
2023-07-22 15:15:51,236 fail2ban.utils [16741]: ERROR 7ff463a21ed0 -- returned 13
2023-07-22 15:15:51,237 fail2ban.actions [16741]: ERROR Failed to execute ban jail 'frps-ssh-ban' action 'firewallcmd-ipset' info 'ActionInfo({'ip': '117.141.150.30', 'fid': <function <lambda> at 0x7ff4628911b8>, 'family': 'inet4', 'raw-ticket': <function <lambda> at 0x7ff462891758>})': Error starting action Jail('frps-ssh-ban')/firewallcmd-ipset: 'Script error'
麻烦大佬看看,顺便问下收到回复会邮箱提醒吗?
@gaga 看了下报错信息:
1. Set cannot be created: set with the same name already exists
2. Error: COMMAND_FAILED: '/usr/sbin/iptables-restore -w -n' failed: iptables-restore: line 2 failed
表明尝试创建的ipset已经存在,并且iptables恢复命令失败,所以你是不是有什么相同的配置,还是说你测试的时候手动创建了它
@Alain 我是阿里云服务器,只开了firewalld和fail2ban,挂了两天发现这封禁毫无效果啊,被一个IP连了几万次都没有封
frps.log:
2023/07/24 19:03:59 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:52206]
2023/07/24 19:04:31 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:37024]
2023/07/24 19:05:03 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:50074]
2023/07/24 19:05:36 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:34892]
2023/07/24 19:06:07 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:47942]
2023/07/24 19:06:38 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:60992]
2023/07/24 19:07:10 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:45810]
2023/07/24 19:07:41 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:58860]
2023/07/24 19:08:13 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:43676]
2023/07/24 19:08:24 [I] [proxy.go:189] [e21c0492b4e04910] [clash] get a user connection [139.162.204.182:46750]
2023/07/24 19:08:44 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:56726]
2023/07/24 19:09:16 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:41544]
2023/07/24 19:09:48 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:54594]
2023/07/24 19:10:18 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:39410]
2023/07/24 19:10:50 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:52458]
2023/07/24 19:11:22 [I] [proxy.go:189] [e21c0492b4e04910] [ssh] get a user connection [2.57.122.150:37276]
fail2ban.log:
2023-07-24 19:08:25,030 fail2ban.filter [16741]: INFO [frps-clash-ban] Found 139.162.204.182 - 2023-07-24 19:08:24
2023-07-24 19:08:44,992 fail2ban.filter [16741]: INFO [frps-ssh-ban] Found 2.57.122.150 - 2023-07-24 19:08:44
2023-07-24 19:09:17,024 fail2ban.filter [16741]: INFO [frps-ssh-ban] Found 2.57.122.150 - 2023-07-24 19:09:16
2023-07-24 19:09:17,319 fail2ban.actions [16741]: WARNING [frps-ssh-ban] 2.57.122.150 already banned
2023-07-24 19:09:49,057 fail2ban.filter [16741]: INFO [frps-ssh-ban] Found 2.57.122.150 - 2023-07-24 19:09:48
2023-07-24 19:10:19,088 fail2ban.filter [16741]: INFO [frps-ssh-ban] Found 2.57.122.150 - 2023-07-24 19:10:18
2023-07-24 19:10:51,120 fail2ban.filter [16741]: INFO [frps-ssh-ban] Found 2.57.122.150 - 2023-07-24 19:10:50
2023-07-24 19:10:51,407 fail2ban.actions [16741]: WARNING [frps-ssh-ban] 2.57.122.150 already banned
2023-07-24 19:11:22,351 fail2ban.filter [16741]: INFO [frps-ssh-ban] Found 2.57.122.150 - 2023-07-24 19:11:22
2023-07-24 19:11:54,384 fail2ban.filter [16741]: INFO [frps-ssh-ban] Found 2.57.122.150 - 2023-07-24 19:11:53
jail.local:
[DEFAULT]
ignoreip = 127.0.0.1/8
bantime = 86400
findtime = 300
maxretry = 5
backend = auto
banaction = firewallcmd-ipset
action = %(action_mwl)s
# FRP SSH防爆破
[frps-ssh-ban]
enabled = true
findtime = 3m
maxretry = 3
filter = frps-ssh-ban
logpath = /root/frp_0.48.0/frps.log
port = http,https
action = %(action_mwl)s
@gaga port = http,https
你指定了80跟443,但是显然你的SSH穿透不会在80或443端口上面,你可以直接修改为
port = all
@gaga 如果你的邮箱是正确的,就会自动给你发送邮件,实在解决不了你发个邮箱给我,我给你个GPT
@Alain leohex711@gamil.com 这是我的邮箱,感觉这问题不好问啊,主要我也是小白,不知道哪里的问题